
Who’s Responsible for PCI Compliance of Your Cloud Workload
This is part 1 of seven-part series on achieving PCI compliance in the cloud.
Shared Responsibility isn’t as easy as it sounds
When businesses sign a service level agreement with a cloud provider, they may believe the provider will protect everything in their cloud− infrastructure and applications alike.
But in each contract there is a clause about shared responsibility that says the cloud provider is responsible only for the security of the infrastructure. That’s their share of the responsibility. But you are responsible for your own data.
PCI seems like it only covers the applications processing primary account number (PAN) data. But in reality, anything that stores or processes PAN, such as content delivery networks (CDNs), backups, connected workstations, web application firewalls (WAFs), and storage systems, such as S3 buckets, are also in scope. That means that workload security is your share of the responsibility. If you aren’t aware of that, you can’t meet your PCI requirements.
What is your PCI compliance responsibility?
Businesses that shift their computing to the cloud need to be aware they are still responsible for:
- Configuring and managing security controls
- Updating and patching software
- Maintaining a firewall
- Encrypting data in-transit and data at-rest
Shared Responsibility in the Cloud
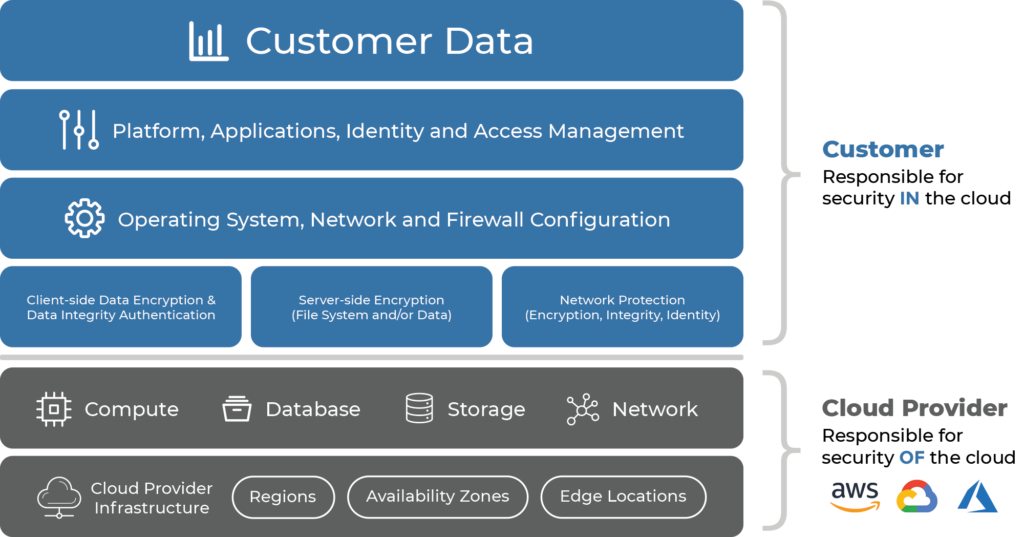
PCI Readiness indicators
If you feel confident in your cybersecurity posture, you may believe you’ve got your share of PCI responsibility under control. And that might be true − but for most organizations, it won’t be. Visibility, an understanding of the ecosystem, and, although it seems obvious, a clear grasp of exactly where the cloud provider’s responsibility ends and yours begins are the base level of PCI cloud compliance.
Visibility Maturity. Do you know what systems you have running in the cloud — not just as designed, but as actually deployed in the wild?
Ecosystem Awareness. Do you understand ALL the systems that touch your PAN?
Your Understanding of Shared Responsibility. Are you clear on what you’re responsible for managing and what your cloud provider is responsible for managing?
5 Strategies to Prioritize
Compliance is not a one-off event. It’s a process that even the most confidently compliant organizations can improve by using these strategies.
- Ensure compliant configuration of your cloud infrastructure.
- Deploy cloud security technologies to ensure the compliance of workloads prior to deployment.
- Ensure continuous monitoring to protect against drift — security is a process, not an event.
- Ensure you have reporting in place to demonstrate your security controls are actually working.
- Ensure your security controls are implemented in a way that can be used in a dynamic scaling environment. You don’t want to scale bad behavior.
The Takeaway
Your cloud provider offers a compliant environment, assuming it’s configured properly — but you are always responsible for your workload. Remember that you can be PCI compliant without being secure. Implement compliance measures with an eye towards the ultimate goal of being secure.
Develop your PCI compliance action plan with our free guide: PCI Compliance in the Cloud, a Practitioner’s Toolkit.
Free Guide: PCI Compliance in the Cloud, a Practitioner’s Toolkit.
